How to Prepare for a Third-Party Data Audit
A notice for a third-party data audit can feel stressful. In fact, a data audit is a health checkup for your data. An outside expert comes in to see how you collect, use, and protect information.

This guide will walk you through how to prepare for a third-party data audit. We will break it down into simple, actionable steps. You will learn what to expect and what to fix first, so you can pass your audit with confidence.
Step 1: Know the Scope and Purpose of the Audit
Before you start pulling files and calling meetings, you need to understand the audit itself. Not all audits are the same. You must know why it's happening and what the auditors will look at. This is the most important first step.
What to Do:
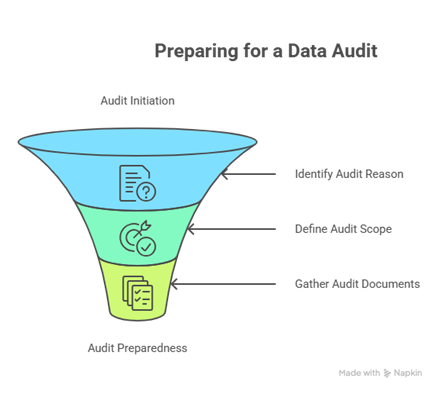
Example:
Imagine your company provides marketing software to a large bank. The bank sends you a notice for a third-party data audit.
- The "Why": The bank needs to ensure its vendors (you) are handling its customer data safely. This is part of their own vendor risk management.
- The "What": The scope is limited to only the bank's customer data that your software processes. They don't care about your employee data or data from your other clients. They will focus on how you collect, store, and protect that specific set of information.
By knowing this, you can focus your energy on the right areas and not waste time preparing things the auditors won't even ask for.
Step 2: Form Your Internal Audit Response Team
You cannot prepare for a data audit alone. It takes a team. You need people from different departments who understand different parts of your data puzzle.
What to Do:
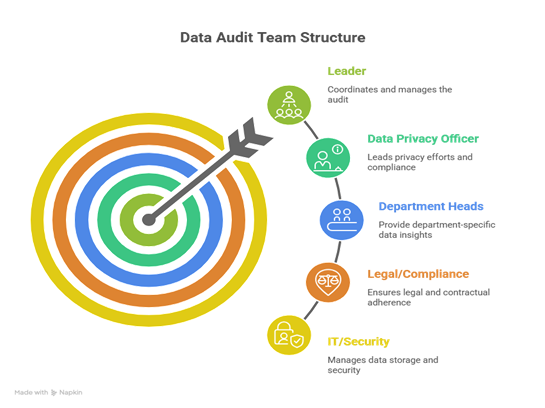
Example:
For the audit requested by the bank, your response team might look like this:
- Leader: Your Data Privacy Officer.
- Team Members:
- An IT Security Manager who manages the servers where the bank's data is stored.
- A lawyer who reviewed the contract with the bank.
- The Product Manager for the software the bank uses.
This team has all the knowledge needed to answer the auditors' questions accurately.
Step 3: Map Your Data; Know Where Everything Lives
This step is often the most work, but it is also the most valuable. You need to create a "data map." A data map is a simple chart or document that shows the journey of data through your company. Auditors love data maps because they provide a clear picture of your practices.
What to Do:
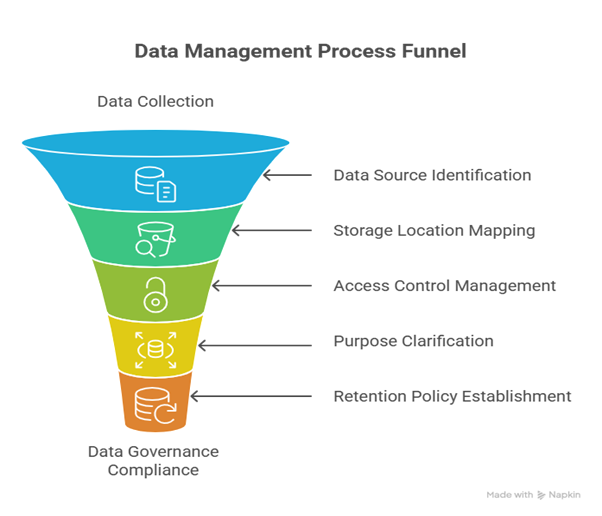
Example Data Map (Simplified Table):
|
Data Type |
Source |
Storage Location |
Who Has Access |
Retention Period |
|
Customer Email |
Website signup form |
Mailchimp,
Salesforce |
Marketing Team |
5 years after last
contact |
|
Customer Address |
Checkout page |
Internal SQL
Database |
Fulfillment Team |
7 years for tax
records |
|
IP Address |
Website visit |
Google Analytics |
Marketing Analytics
Team |
26 months |
This map will immediately show you (and the auditors) where your risks might be. It is the foundation for a successful data governance program.
Step 4: Review Policies, Procedures, and Contracts
Auditors don't just look at your systems; they look at your rules. They want to see your written policies and legal agreements to make sure they are complete and up to date. This is where you can fix problems before the audit even begins.
What to Fix First:
If these policies don't exist, write simple versions now. If they are old, update them to reflect your current practices.
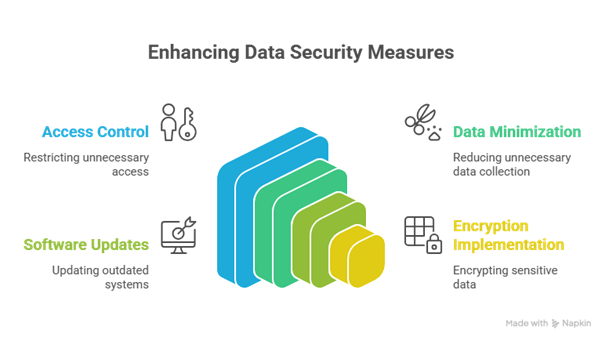
Step 5: Conduct a Pre-Audit and Fix Obvious Gaps
Now that you have your data map and reviewed your policies, you can find your own problems before the auditors do. Run a "mini audit" on yourself. Go through your data map and checklist and look for easy-to-fix issues.
What to Fix First (High-Priority Checklist):
- Access Control: This is often the easiest win. Are former employees still able to log in? Does your entire marketing team have access to sensitive financial data they don't need? Remove unnecessary access right away. Restrict access to a "need-to-know" basis.
- Data Minimization: Are you collecting data you don't use? For example, if you ask for a phone number on a newsletter signup form but never call anyone, stop asking for it. Collecting less data means less risk.
- Outdated Software: Are your servers, websites, or applications running on old, unsupported software? This is a major security risk. Prioritize updating and patching critical systems.
- Lack of Encryption: Is sensitive data being stored as plain text? Data should be encrypted both when it’s stored (at rest) and when it’s moving (in transit). Work with your IT team to encrypt sensitive data fields.
Fixing these obvious problems shows auditors that you take data protection seriously.

This content is AI-assisted and reviewed for accuracy, but errors may occur. Always consult a legal/financial professional before making business decisions. nrold.com is not liable for any actions taken based on this information.


